Engineers at Southwest Research Institute have identified a computer vulnerability for electric vehicles using DC fast charging systems
Cyber security and electric cars, where you need to raise the guard
Cybersecurity is inevitably a top priority in an increasingly digital and interconnected world. And after deepening the report linking photovoltaic and cybersecurity, and following the creation of the first network code to assess the computer risk of the European electric system, the focus is now shifted to electric vehicles. A team of engineers at the Southwest Research Institute, Texas, has identified a cybersecurity vulnerability in electric cars. Or, more specifically, those that use continuous current fast charging systems (CC).
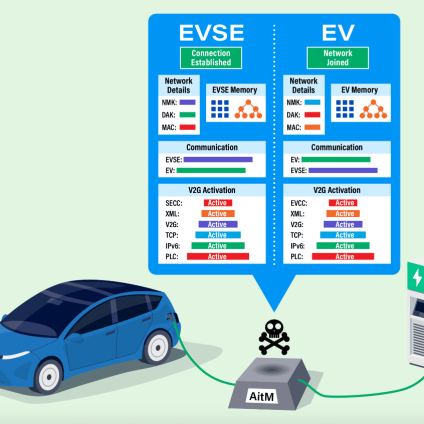
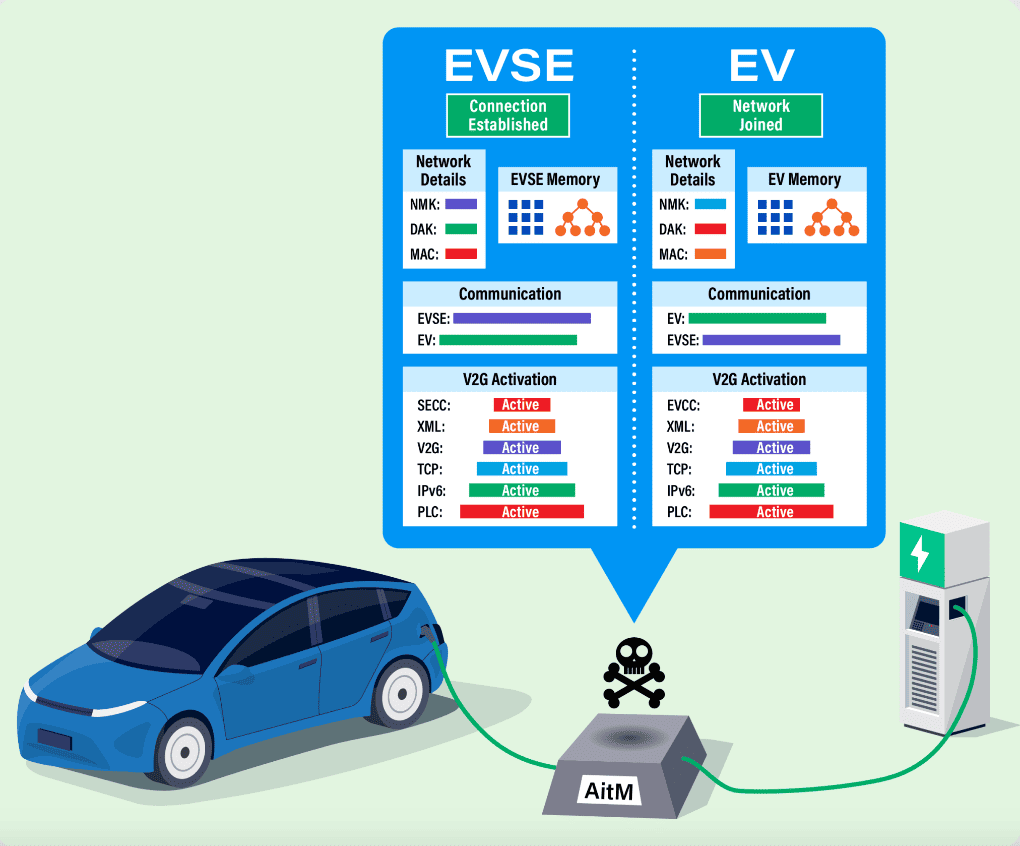
This technology today represents the most widespread and efficient way to power the battery of an electric vehicle, but to do its job it needs communication protocols. Both the low-level ones manage the recharge phase, and the high-tier ones are entrusted with more complex tasks, such as managing tariffs and payments. The latter category includes the PLC or power line communication protocol, a data transmission technology that uses the power supply network as a transmission medium. The protocol is used in CCS1 and CCS2 to start charging devices and equipment. What does it transmit? A wide range of data, from load status to vehicle identification number.
The Powerline protocol vulnerability.
“Through our tests, we found that the PLC layer is poorly protected and lacks encryption between the vehicle and the chargers,” said Katherine Kozan, the engineer who led the project for SwRI’s High-Reliability Systems department. To be precise, the team discovered a generation of unsafe keys on older chips during tests, confirmed through online searches as a known problem. The institute exploited vulnerabilities in the PLC level to access the network key and digital addresses of both the chargers and the vehicle using an Adversary-in-the-Middle (AitM) attack that can emulate both the electric vehicle and the charging equipment.
The research is part of SwRI’s commitment to helping the mobility sector and the government improve automotive cybersecurity, a broad sector that embraces integrated car computers and smart-grid infrastructure. The first steps were taken in 2020 with a project that allowed the hacking of a J1772 charger, interrupting the charging process with a laboratory-built spoofing device (a type of cyber attack that employs identity forgery).
In the latest research, SwRI explored vehicle-network charging (V2G) technologies governed by ISO 15118 specifications for communications between electric vehicles and electric vehicle power supply equipment (EVSE) to support the transfer of electric energy.
“As the network evolves to accommodate more electric vehicles, we need to defend our critical network infrastructure from cyber attacks, while ensuring payments to recharge electric vehicles,” said Vic Murray, SwRI’s Deputy Director of High Reliability Systems. “Our research has found room for improvement.”
Electric vehicles: a zero-trust architecture
So, how can we improve cybersecurity for electric cars? An “immediate” solution could be to add encryption to the network membership key to protect the V2G recharge process. However, this approach is not without challenges. Additional levels of encryption and authentication could even become a security threat. For example, an authentication or decryption error could disrupt a vehicle’s functionality or performance.
That’s why scientists are developing a zero-trust architecture that can address these and other challenges. The system connects several embedded systems using a single cyber security protocol. SwRI’s future EV cybersecurity research will test zero-trust systems for PLCs and other network levels.